This article explains the legacy version of
A profile defines the set of security restrictions that may be used to screen inbound HTTP/HTTPS traffic.
Learn:
Threat Detection (Legitimate Traffic)
A profile defines the criteria for determining whether traffic is legitimate or malicious. WAF leverages this security configuration and performs a sequential check for each criterion. An overview of this security check is provided below.
- Does the request meet a whitelist criterionA whitelist identifies traffic that should always be considered safe. Traffic may be whitelisted by ASN, country, IP address, referrer, URL, user agent, HTTP method, media type, and/or file extension.? If so, it is considered legitimate and no further checks will be performed.
-
Proceed to the next step if your profile configuration does not contain at least one acceslist.
Does the request satisfy at least one criterion in each defined accesslistAn accesslist identifies traffic that may access your content upon passing a threat assessment. Traffic may be accesslisted by ASN, country, IP address, referrer, URL, user agent, HTTP method, media type, and/or file extension.? If not, then the request is identified as a threat and no further checks will be performed.
- Does the request meet a blacklist criterionA blacklist identifies traffic that should always be considered malicious. Traffic may be blacklisted by ASN, country, IP address, referrer, URL, user agent, HTTP method, media type, and/or file extension.? If so, it is considered malicious and no further checks will be performed.
- Will the request be served from cache instead of being forwarded to an origin server? If so, it is considered legitimate and no further checks will be performed.
- The request will undergo threat detection analysis according to the profile's core rule set and its delivery profile. A request will be classified as malicious traffic when the severity and frequency of rule violations exceeds the configured threshold.
How Does It Work?
A request will not be considered a threat until a threshold of violations is met. The score assigned to a request is determined according to the severity and frequency of the violations.
-
Severity: Each rule is assigned a severity. Each severity is assigned an anomaly score from 2 to 5.
Severity Anomaly Score Description Critical
5
This severity level is triggered by web attack violations.
Error
4
This severity level is reserved for future use.
Warning
3
This severity level is triggered by malicious client violations.
Notice
2
This severity level is generally used to indicate protocol policy violations.
- Frequency: A threat is identified when the aggregate score for all violations meets or exceeds the configured threshold value. This allows WAF to account for minor violations without forcing it to take action for a single offense.
The workflow for threat detection is illustrated below.
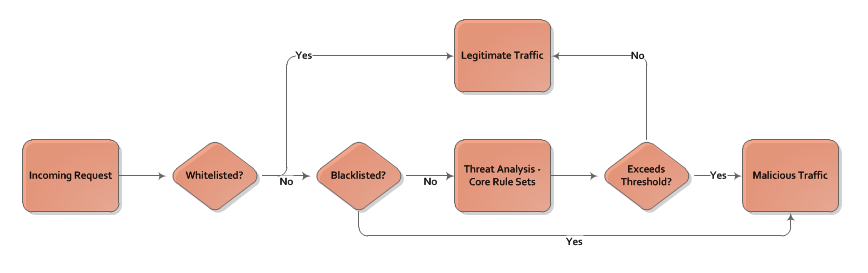
A profile may be assigned a threshold value from 2 to 20. However, the recommended value is 5. A threshold value of 5 triggers threat identification after a single severe violation or multiple minor violations. This balanced approach identifies questionable requests without impacting legitimate traffic.
Production Traffic
By itself, a profile will not affect production trafficRefers to requests directed to a live site. For example, the HTTP requests generated when a user visits your web page is considered production traffic.. It requires both of the following conditions:
-
An instance must define:
- A profile through which production traffic will be screened.
- The action that should take place in response to threats detected in production traffic.
-
The above instance must be activated for the desired type of traffic from within Rules Engine via the Web Application Firewall feature.
More Information