This article explains the legacy version of
The configuration of Web Application Firewall consists of three sequential steps. Once all three steps have been performed, near-real-time threat monitoring may be performed through the dashboard. A brief overview for each WAF setup step is illustrated below.
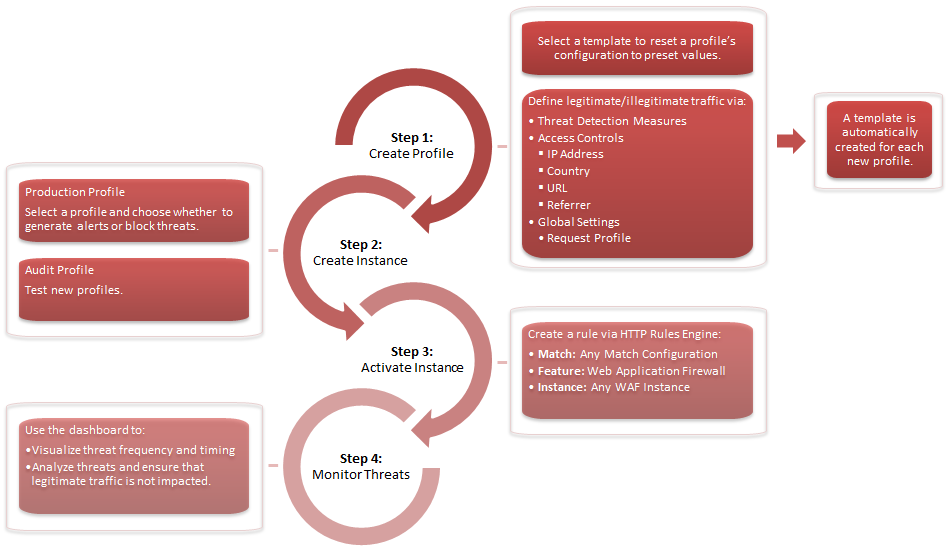
Additional information on each WAF configuration step is provided below.
| Step | Name | Description |
|---|---|---|
|
1 |
Define a security policy for inbound HTTP/HTTPS traffic that defines the:
|
|
|
2 |
Select the profiles that may be applied to site traffic and the manner in which detected threats may be handled. An instance defines:
|
|
|
3 |
Define both of the following items through Rules Engine:
|
Different types of requests may require varying levels of protection. Create a profile and an instance for each type of request that requires a unique level of protection.
More Information