This article explains the legacy version of
Many web sites, web applications, and web servers receive and process requests from outside a company's protected internal network. As a result, they are vulnerable to a variety of malicious attacks including SQL injections, cross-site scripting, and application layerTCP/IP: Refers to the layer that supports applications and processes. For example, it contains protocols (e.g., HTTP and FTP) that facilitate communication across a network. distributed denial of service (DDoS).
This exposure poses a threat to your infrastructure and the confidentiality, integrity, and availability of the data delivered by those resources over the Internet. These types of attacks can result in unauthorized access to content, the loss of personally identifiable information (PII), and the dissemination of private/copyrighted information.
The Web Application Firewall (WAF) service provides a layer of security between many of these security threats and your external web infrastructure. Our WAF increases security by monitoring, detecting, and preventing application layer attacks. It inspects inbound HTTP/HTTPS traffic against reactive and proactive security policies and blocks malicious activity in-band and on a real-time basis.
There are various layers to the protection provided to an origin server via Web Application Firewall, such as:
- Inherent protection from DDoS attacks.
- Our worldwide presence establishes an imposing and extensive barrier between an origin server and malicious traffic, regardless of whether it consists of a high-volume HTTP GET flood attack or a slow DDoS attack.
- Protection from application layer attacks.
- Enable a comprehensive set of threat detection measures for the purpose of identifying malicious traffic. These measures define the types of application layer attacks that will be detected, such as:
- Protocol validation
- Malicious client identification
- Generic attack signatures
- Known vulnerabilities signatures
- Trojan/backdoor access
- Denial of Service
- Enable a comprehensive set of threat detection measures for the purpose of identifying malicious traffic. These measures define the types of application layer attacks that will be detected, such as:
-
Filtering out unwanted traffic by screening for a custom delivery profile.
Traffic that doesn’t meet the requirements defined in this HTTP delivery profile may be blocked before it even reaches our core network.
-
Establishing traffic restrictions to block malicious traffic.
Use a whitelist, blacklist, or accesslist to restrict traffic by by ASN, country, IP address, referrer, URL, user agent, HTTP method, media type, and/or file extension.
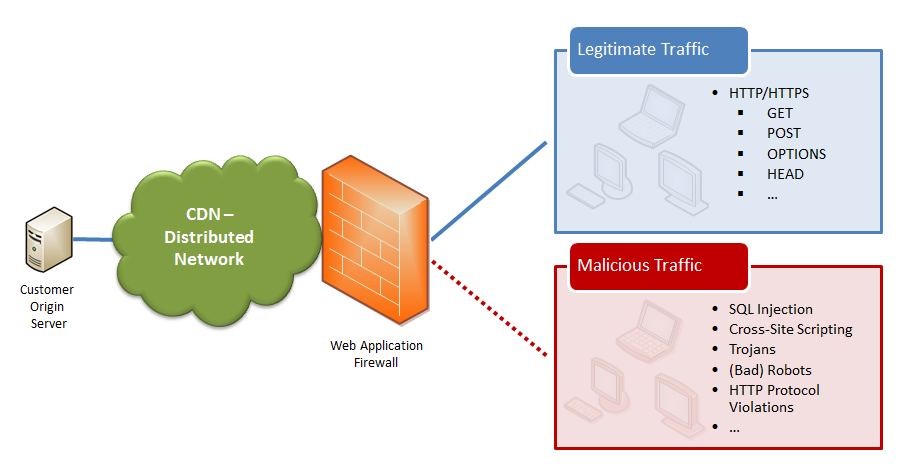
How Does It Work?
The following diagram highlights how traffic is screened before it is processed for delivery. The distributed nature of our worldwide network provides an additional layer of protection to origin servers.
More Information